Data security and reliability are the most critical expectations of a Managed File Transfer solution in our data-driven world. Organizations need to transfer data and files between people, partners, businesses, and applications – without worrying that a file will land in the wrong hands. How people secure MFT looks different than it did ten or twenty years ago: nowadays, teams can rely on predictive monitoring, alerts, and actions backed by machine learning to monitor file transfers and avoid security incidents.
But beyond the technology and features is a principle that you may have heard more about recently: “Zero Trust Architecture”. Technology loves buzzwords and acronyms. Sometimes, Information Security teams make it harder for consumers to understand the impact of unsecure practices. Oftentimes, this leads to catastrophic breaches in compliance, with people figuring out an easier path to work around restrictive security measures.
We’ve all figured out a way of sharing a larger file via Dropbox, or at some point used personal devices to store/retrieve/access sensitive data to ensure the job gets done. The world we live in almost mandates us to figure out a quick way, and Security often forces additional complexity. Who wins or loses in this battle? You know the answer. So how about a quick primer on Zero Trust Architecture.
Data security is getting more complex
This tug of war between Usability (UX), and Security is a battle that puts the actual owners of the data in a precarious position, where they risk gambling away their privacy and confidentiality.
Today, this becomes even more apparent when you consider the magnitude of data being exchanged in the world – we now count it in zetta bytes and even petabytes – and the proliferation of the devices that blur the boundaries of reach. Does the location of the device matter? Does the location of the service provider matter? Can we secure the data regardless of the different ways we are accessing the data
Prior to this innovation cycle of bring your own device (BYOD) into the ecosystem, Information Security Dan Hitchcock eerily predicted the current state of our existence:
“The notion that the data is the asset of greatest interest is certainly not new to the attacker – the data has, ultimately, always been the target of the most successful, prolific, and damaging attacks.”
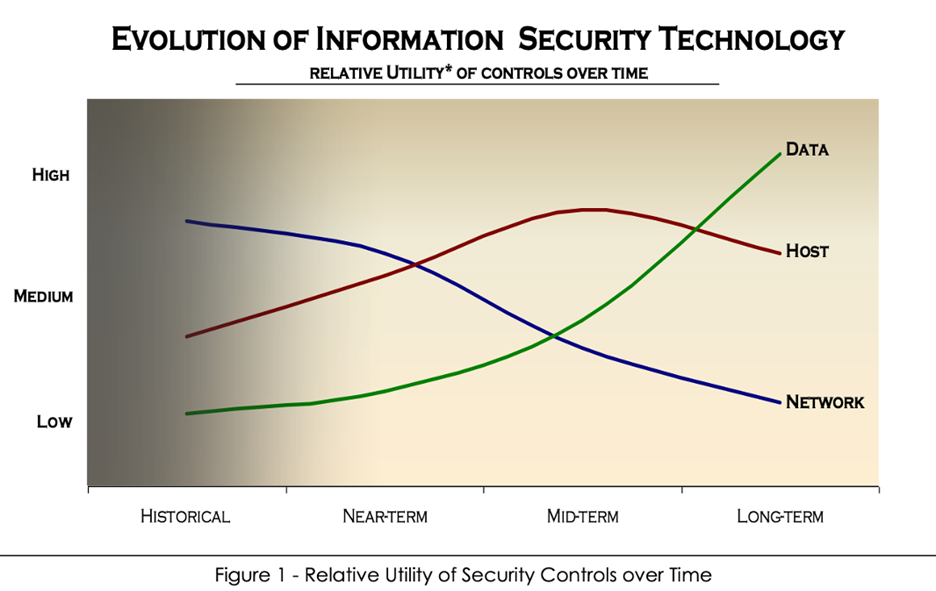
Source: Dan Hitchcock, Evolution of Information Security Technologies 2005
It was always about the data, Stupid!
MFT security must take into consideration the owners of the data
We are desensitized to the effect of data breaches, and the impact they cause to businesses and their consumers are way too many, and way too common. The tolerance to this mind-numbing status quo allowed IT teams to innovate on the wrong problem by putting band-aid measures on the problem and happily masking the severity of the underlying damage.
We blocked and punched holes in firewalls and put a decent-sized perimeter around the datacenter hosting all our apps and services. Of course, this didn’t stop the actors who were already inside the building to cause extensive damage. Shocking.
Cue the mass emails offering identity protection packages to customers when such incidents happen, affecting the brand value of the business. At the end of the day, business is not getting the adequate quality of service from IT departments to process payments, fulfill medications, or run supply chains in a secure, reliable manner. And the damage to their brand perception from the customers is an even bigger hit. Mind-numbing.
The explosion of personal devices courtesy of Apple and Google from a couple of decades ago resulted in introducing more hops and VPNs, thereby creating a very complex networking infrastructure that is designed to fail when you are maxing out the limits. The immediate whip-lash effect from the consumers was to pivot to using something easy and intuitive – of course, unmanageable. We are all equally guilty of using an app that had no security posture. The band-aid in this case was to block the apps. Sigh!
Time and again, the Usability vs. Security tug of wars have proven to be a disaster for users. This is worsening with the rise of cloud service adoption, as now the boundaries are blurred between the ground and cloud – hybrid cloud. DMZ what?
Fortunately, this post is not about doomsday prediction – it’s about doomsday preparation.
Why Zero Trust for MFT security?
It doesn’t have to be this chaotic. It doesn’t need to be this complex to manage. Enterprises are allowed to be open for business – that is the whole point.
Zero Trust Architectures are a great step in the right direction to allow the business teams to innovate, and the technology providers to enable what the business needs. It shouldn’t be any other way. In fact, Zero Trust should be a key skill to help you survive this wave of digital transformation.
What is Zero Trust? Zero Trust is a guiding principle that will allow your brand to be open for business. It allows you to:
- Innovate and compete without having to worry about locking your front door
- Deliver functional, consumable services – without having to worry about VPNs and or the Cloud
- Reduce the risk of data breaches by arming you with the right level of incident management
What is stopping us from implementing Zero Trust principles to secure MFT?
You are right. This should be intuitive. We don’t need to put the consumers of our services at risk of gambling away their privacy.
We can enable that control plane by being ready to shrink the perimeter around the data and resources we are trying to protect. This is akin to asking hotel patrons to swipe their badge every time they are trying to access the gym in the hotel lobby.
Zero Trust guides IT services and service providers in reducing the attack surface and providing the least privileged access. Fine-grained access controls have always been in place, but linking those with a centralized identity management is the hygienic thing to do.
Zero trust is not really about trusting nothing. Zero trust is about verifying everything explicitly. When I access my internal messenger from a new city, the pop up to re-authorize is a price to pay for the risk of gambling with our customers’ data – i.e. the context of where the users are coming from, the anomaly detection, and appropriate response to verify explicitly are done seamlessly behind the scenes. If humans are adept at it, why can’t we tokenize the authorization exchanges for our systems-to-systems interactions?
At Axway MFT, we promise our customers the quality of service needed for running their business-critical workloads. This is at the heart of our objectives to provide the right reliability, efficiency, and security measures that your business needs.